
For many a Wsus seems like a walk, but personally in this months (and maybe years) I have realized that it is not that simple and its implementation is always a challenge! So let’s try to activate our first WSUS!
First, decided where you will place the WSUS update direcotory and db schema (Take in mind that WSUS use a huge space and require a lot of resources to run well (In a small environment you need at lest 1Tb of disk space, 8 Gb ram and 4 cpus)
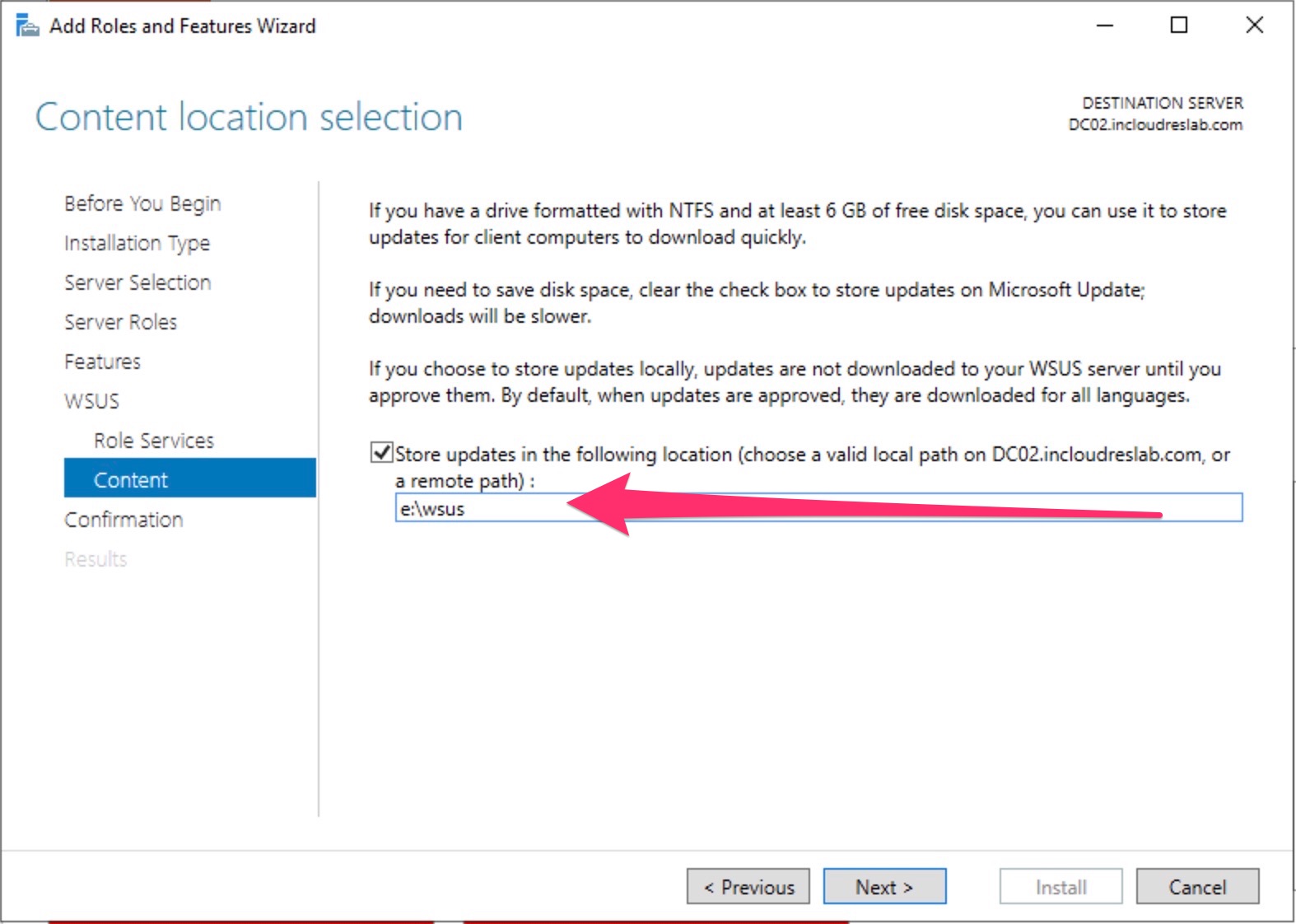
In my case I’ve prepared a folder in e:\WSUS and the systems has 16 Gb ram and 8 vcpu.
Last thing, before you proceed to install the WSUS role you must install the Report Viewer 2012 Runtime and the MsSQL CLT Type.

Install the role.
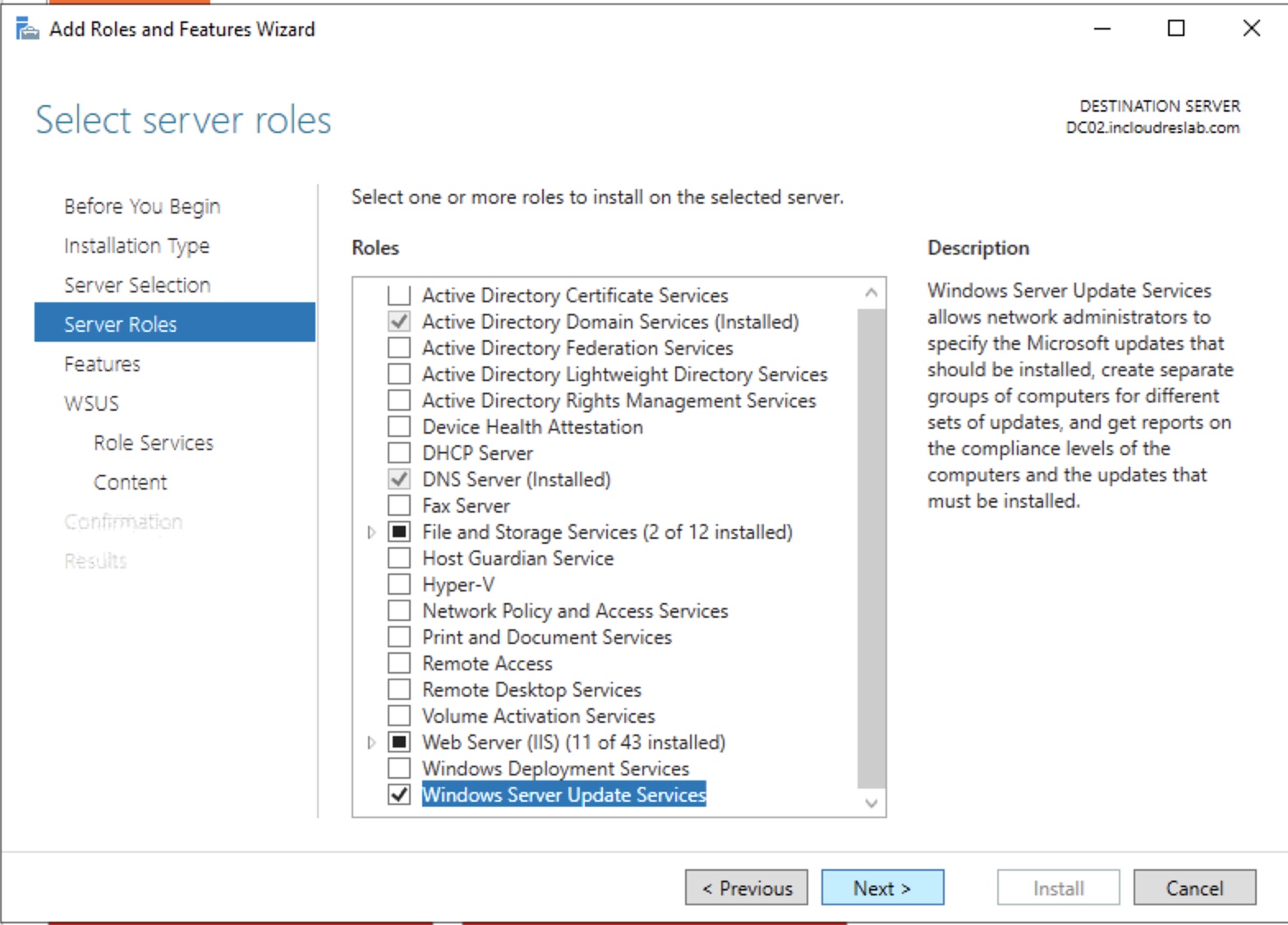
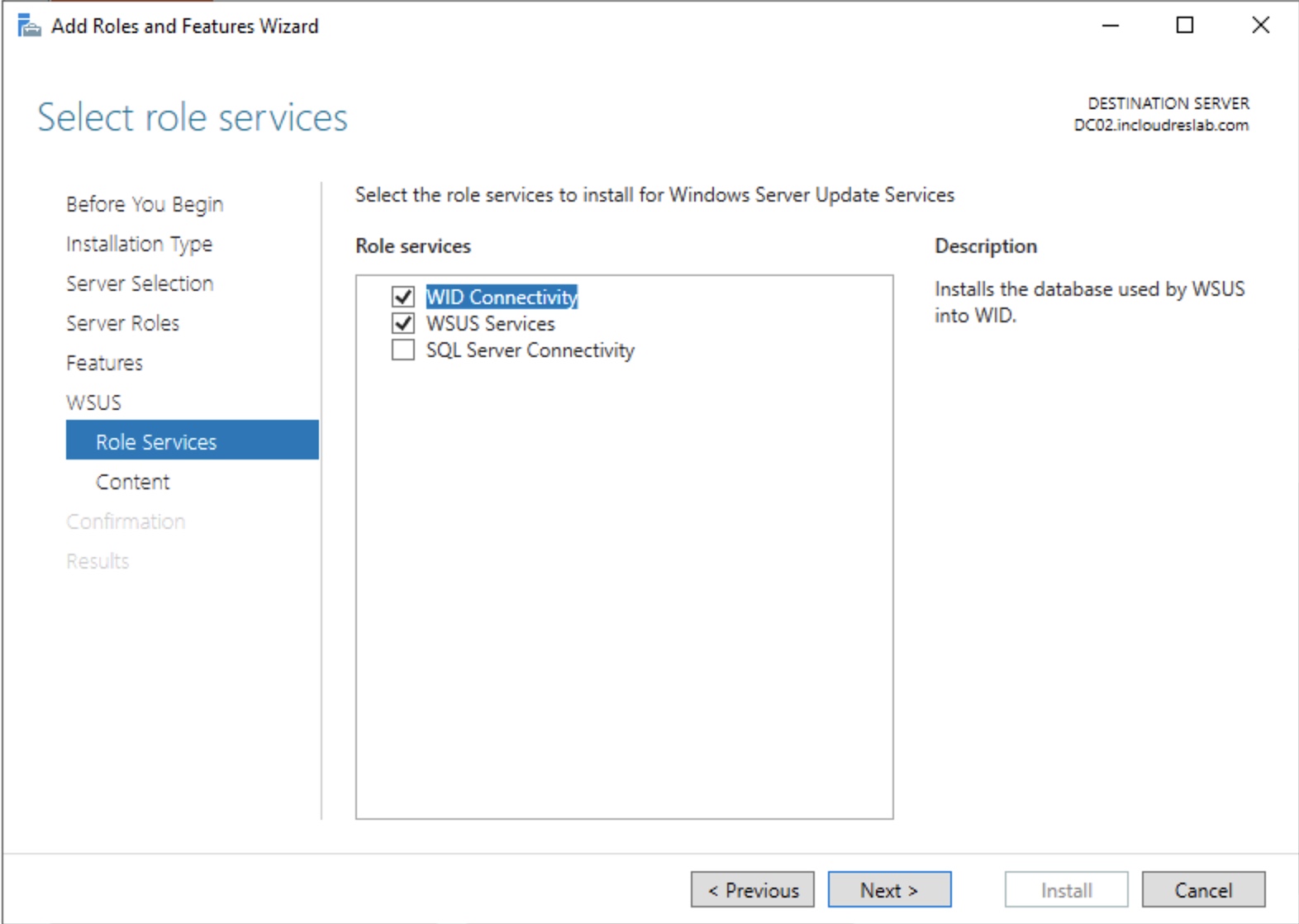
Set the folder for the updates (you must create it)
Install..
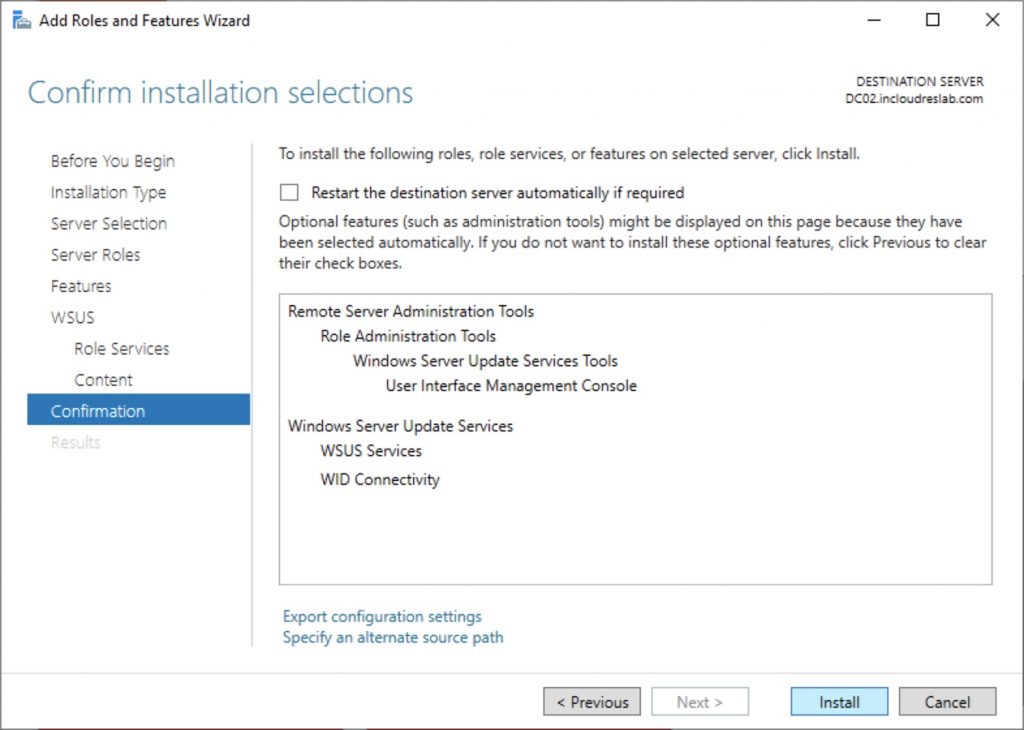
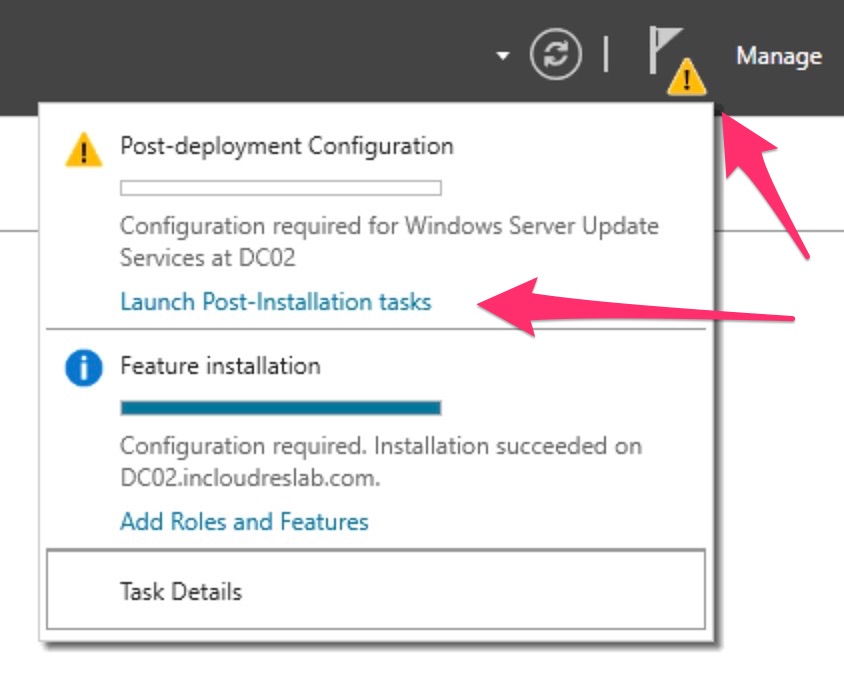
Launch the post installation tasks and wait the completion
Now fallow the wizard to finish the WSUS setup…
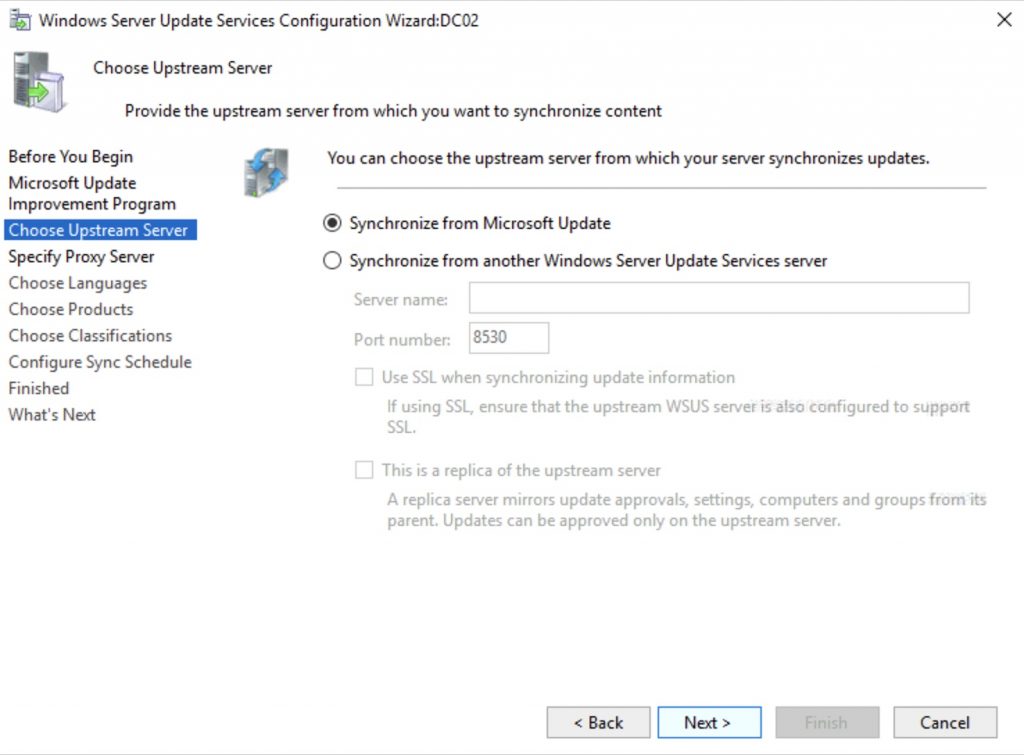
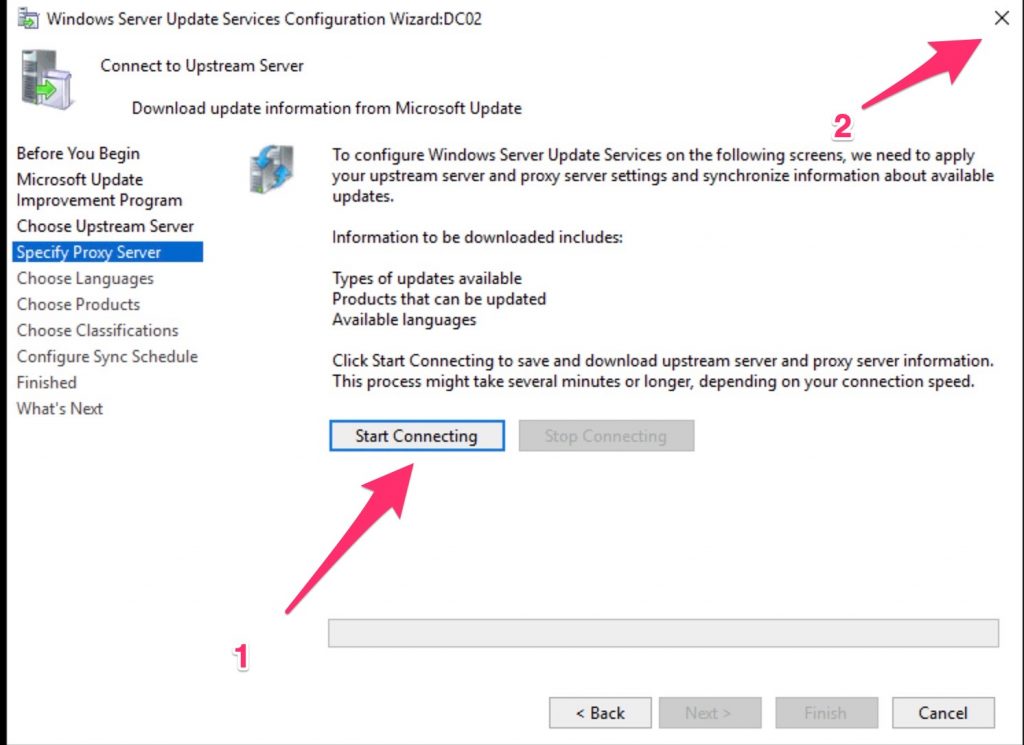
You can chain multiple WSUS, but this is not our case and we are going to get our (the WSUS) updates from Microsoft Update
Now click START and then close the wizard unless you want to wait for hours ….;)
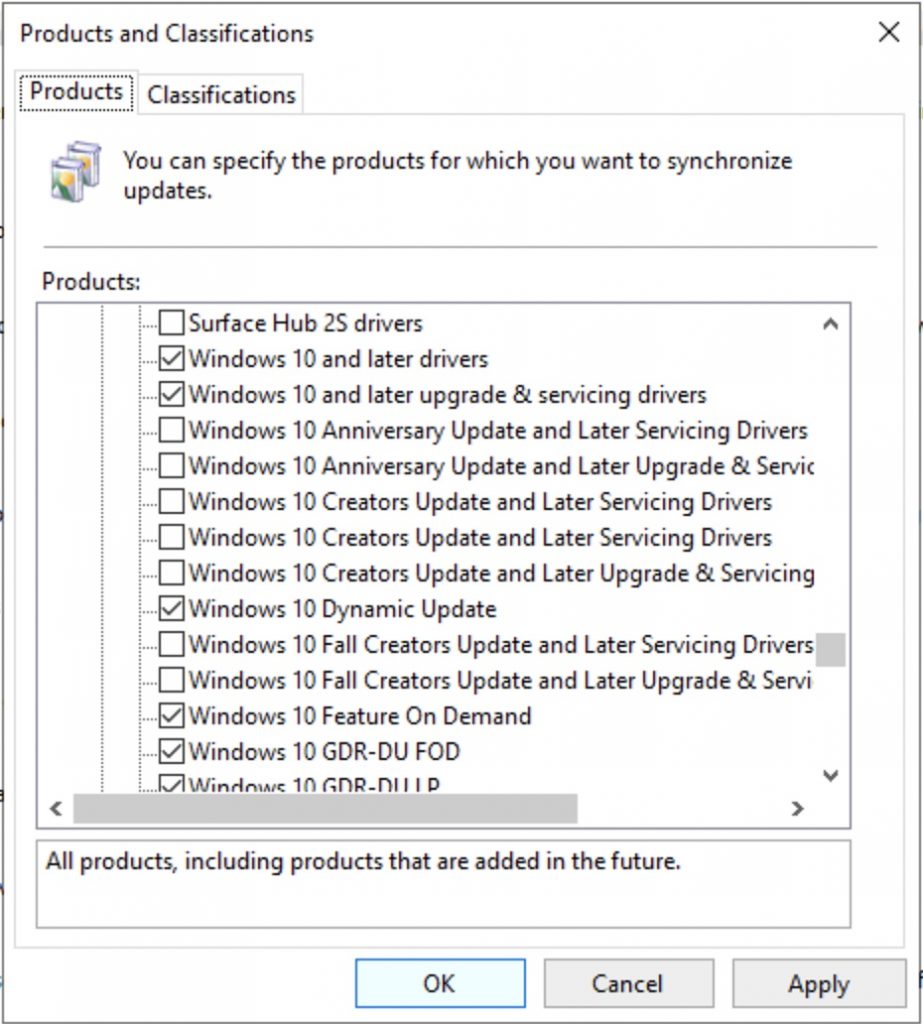
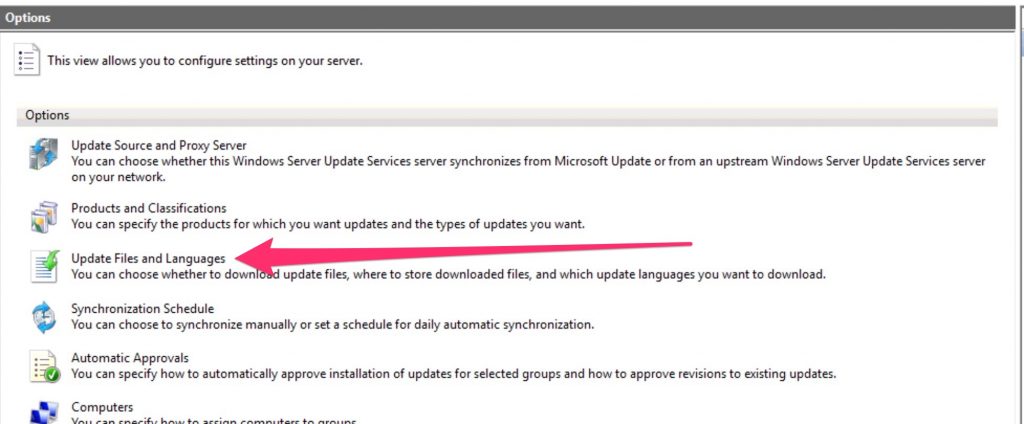
At this point go to the WSUS and set the products for which we need updates… In my case I will choose only Windows 10
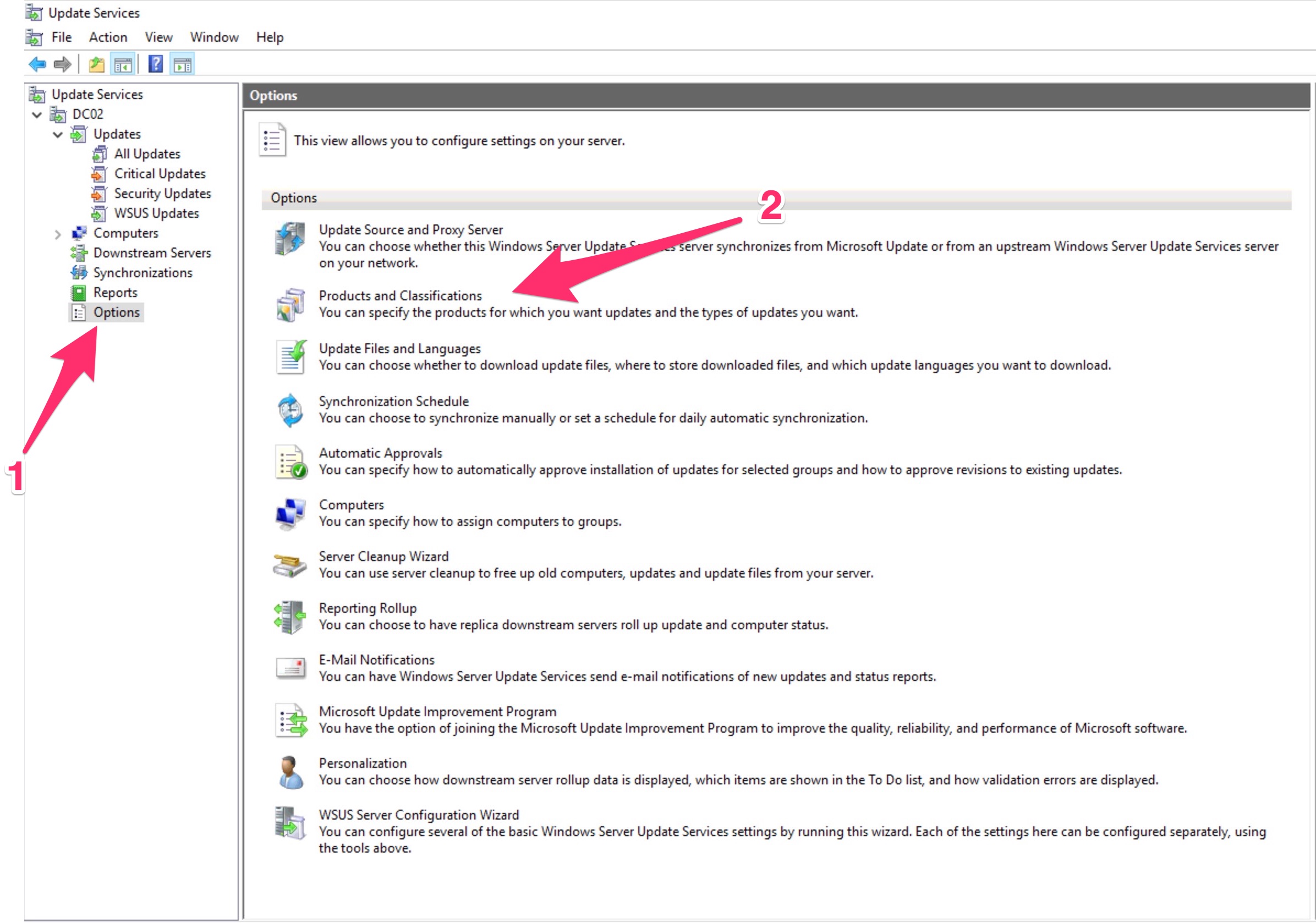
Take in mind that, for Windows 10 these are the meaning of the products (from this interesting post of Ray Jia ) :
Windows 10 Dynamic Update => contains updates to the Setup engine and updates to the servicing stack.
Windows 10 GDR-DU => means General Distribution Release and contains the Dynamic Update versions of cumulative updates.
Windows 10 GDR-DU FOD => also add the Feature on Demand Dynamic Updates that can be added at any time like .NET Framework
Windows 10 GDR-DU LP => as above, but for the actual language packs that change the display language.
Windows 10 Feature on Demand => contains sources to install feature on demand. Mostly language stuff.
Drivers => for use within the running operating system. These contain drivers that can be downloaded and deployed to a running Windows.
Upgrade and servicing drivers => drivers that are used downloaded as Dynamic Updates by the Setup engine during upgrades. The goal of these drivers is to ensure that you have proper compatible drivers after your upgrade, as sometimes certain drivers have issues and need to be updated to work properly.
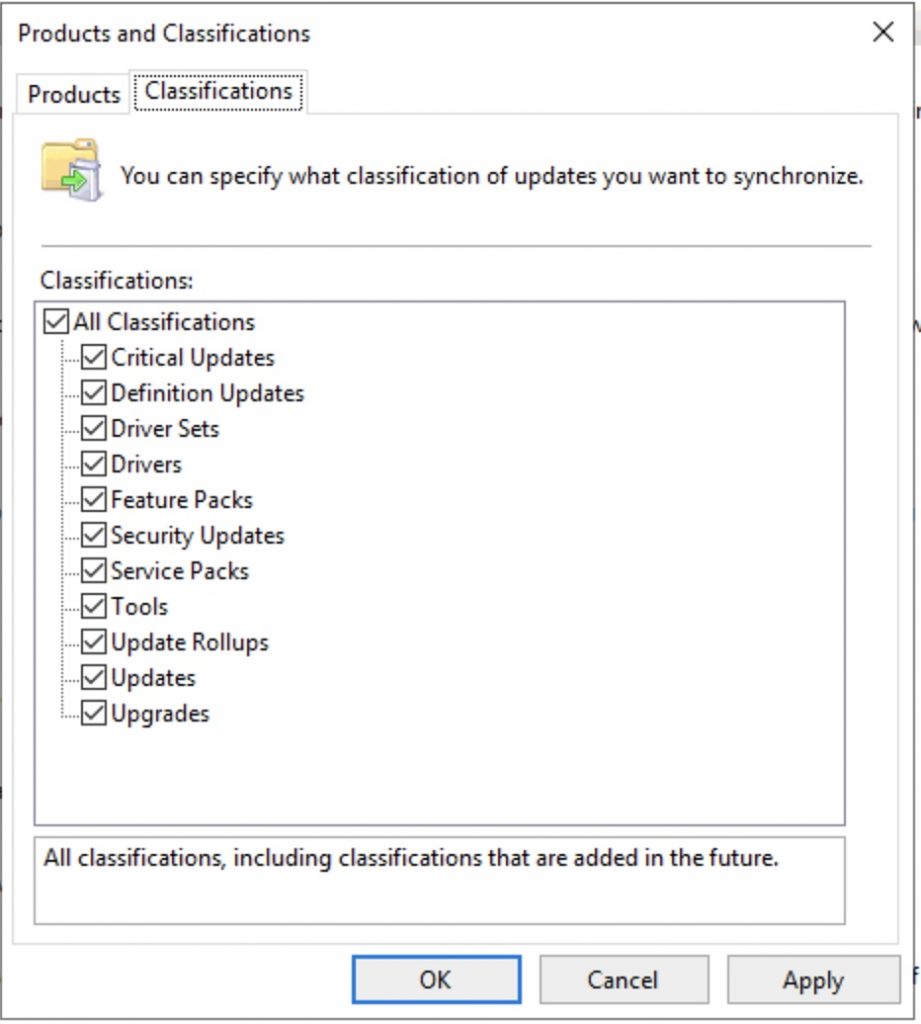
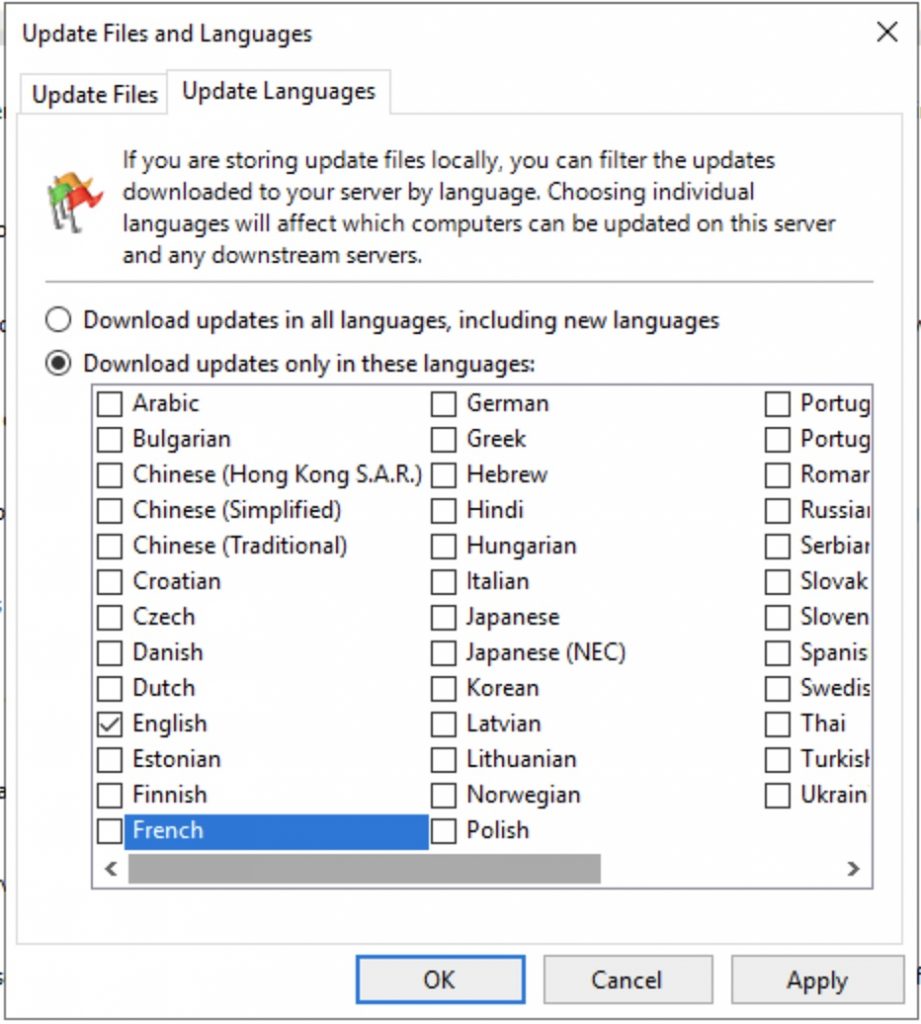
Set the language that you need …
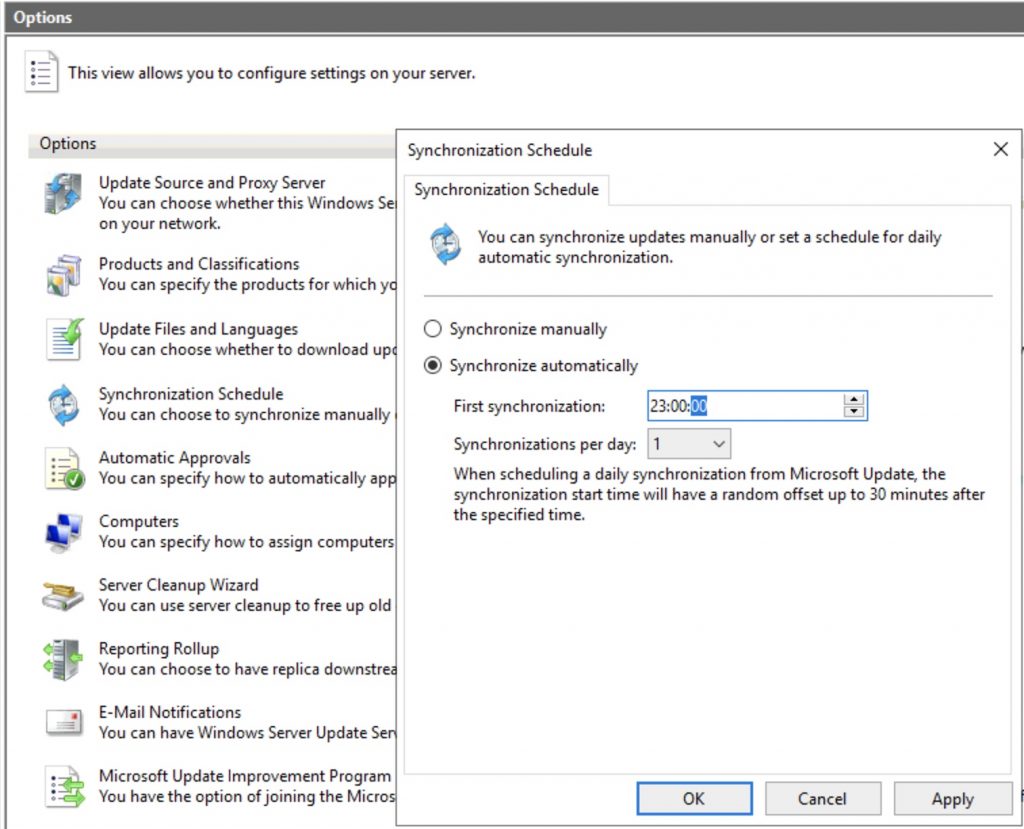
Finally set the sync scheduler…
Now, some useful tips..
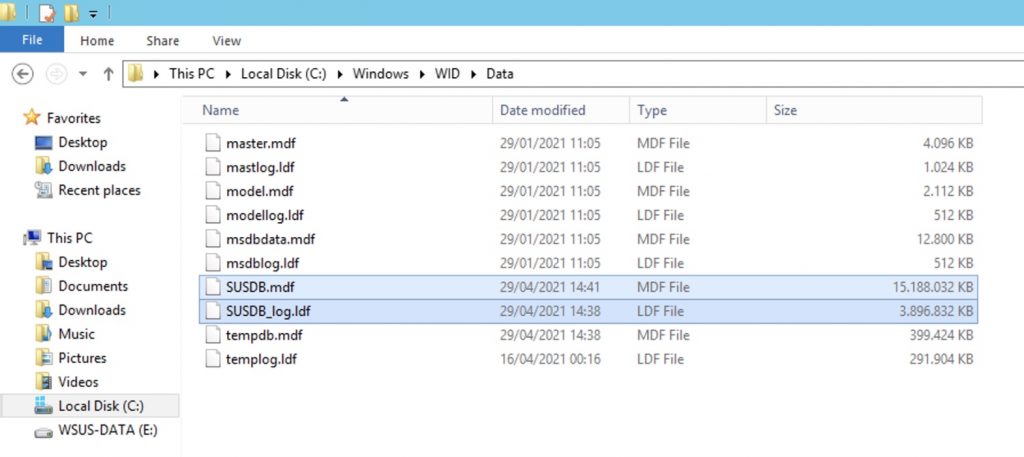
1 ) The location of the WSUS DB is => C:\Windows\WID\Data
2) To force a client to register itself with WSUS, use this commands:
Win7-Windows2008-2021-R2:
wuauclt /resetauthorization /detectnow
This is a reference for the wuauclt.exe
Windows 10 and Windows 2016-2019:
usoclient.exe startscan
3) Other commands that you can use :
usoclient.exe startdownload download updates
usoclient.exestartinstall install updates
usoclient.exeRefreshsettings Refresh settings if any changes were made
usoclient.exeStartInteractiveScan Open a dialog and start scanning for updates
usoclient.exeRestartDevice Restart computer to finish installing updates
usoclient.exeScanInstallWait Scan, Download, and install updates
usoclient.exeResumeUpdate Resume installing updates on next boot
4) To check what parameters you receive from GPO doing this:
RSOP.msc
5) The hive used by Windows Update on a local pc that receive a WSUS GPO
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate
6) To debug client side problems, you could export the Windows Update logs with this command:
Get-WindowsUpdateLog
Finally, I’ll talk about a good GPO to start with .
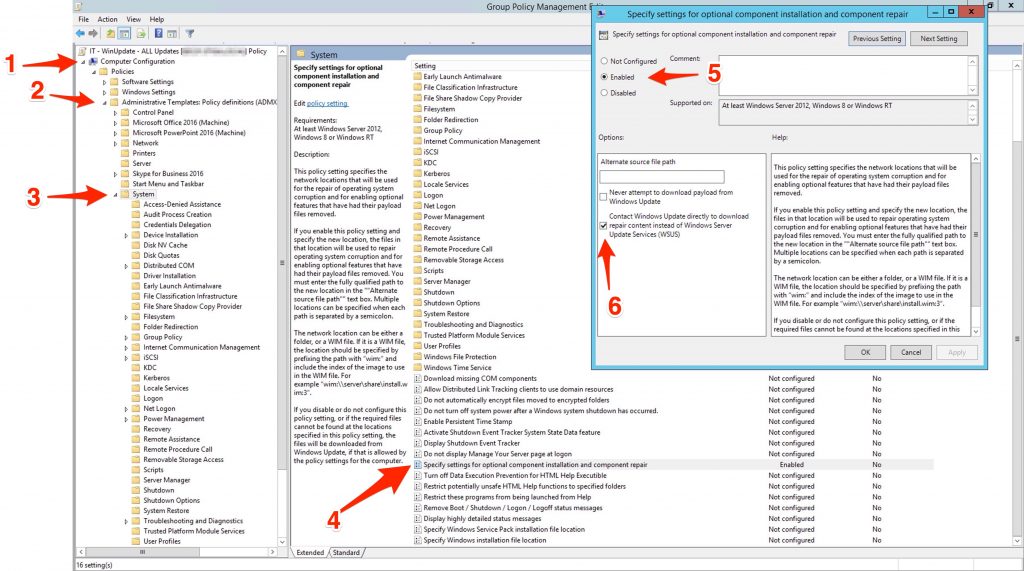
“specify settings for optional component installation and component repair” (Computer Configuration => Administrative Templates => System => Specify settings for optional component installation and component repair setting”
With this setting active, if during an update authorized by the WSUS a component not present in the WSUS is required, in this way the client will be able to download it from the Windows update. If not, then you will see that even the updates are authorized by WSUS these will not install … so enable it !!
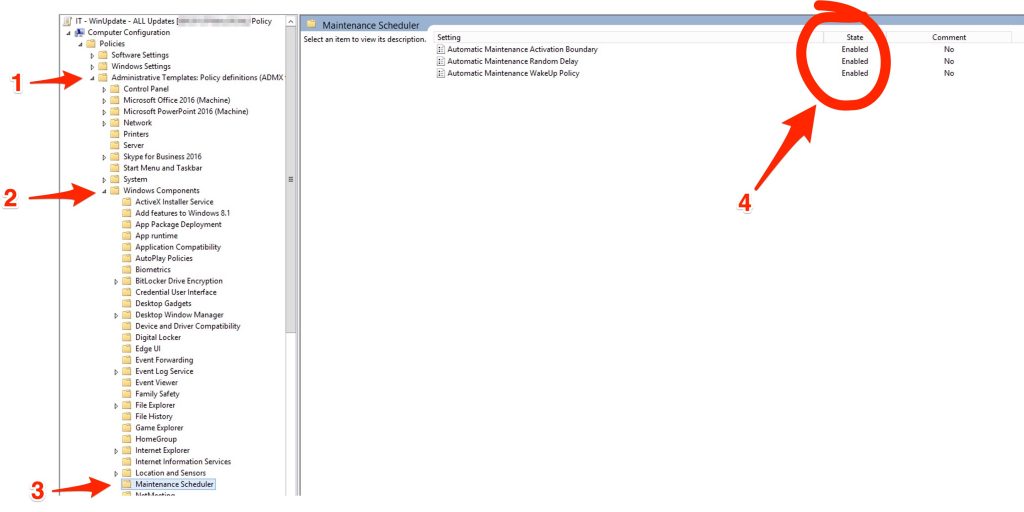
Automatic Maintenance, from Microsoft “maintain the health and performance of a Windows PC. Maintenance includes keeping the Windows operating system (OS) and applications up-to-date..” , so, if you want that a Windows 10 updates itself trought a WSUS , you have to enable it.
Automatic Maintenance Activation Boundary => 2001-01-01T12:00:00
Automatic Maintenance Random Delay => PT4H
Automatic WakeUp Policy => ENABLE
Finally go to the main section Computer Configuration => Administrative Templates => Windows Component => Windows Update
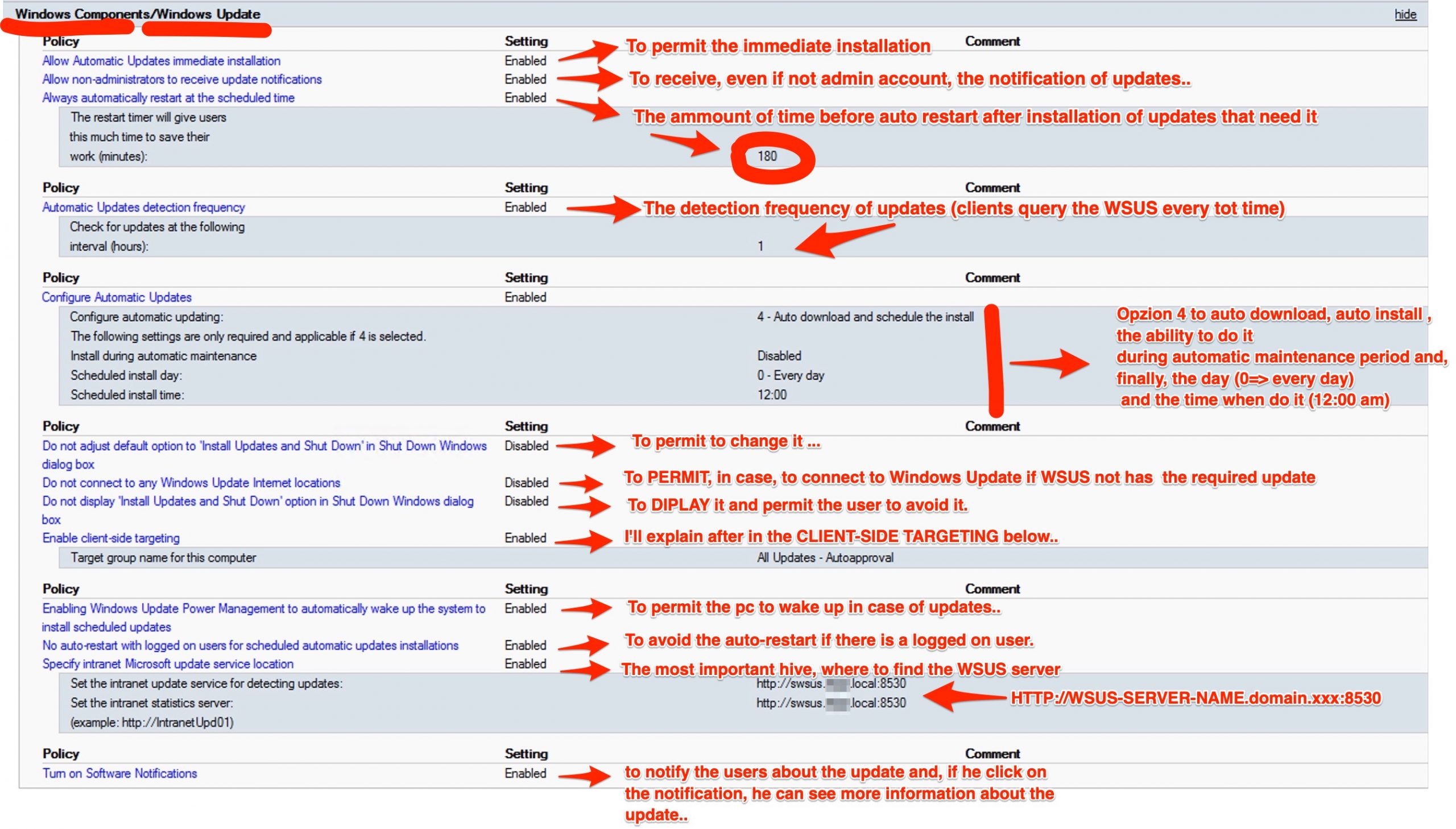
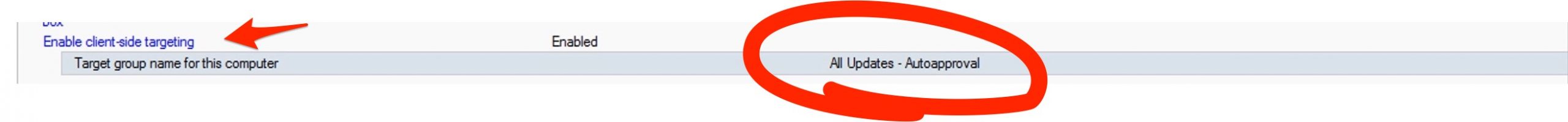
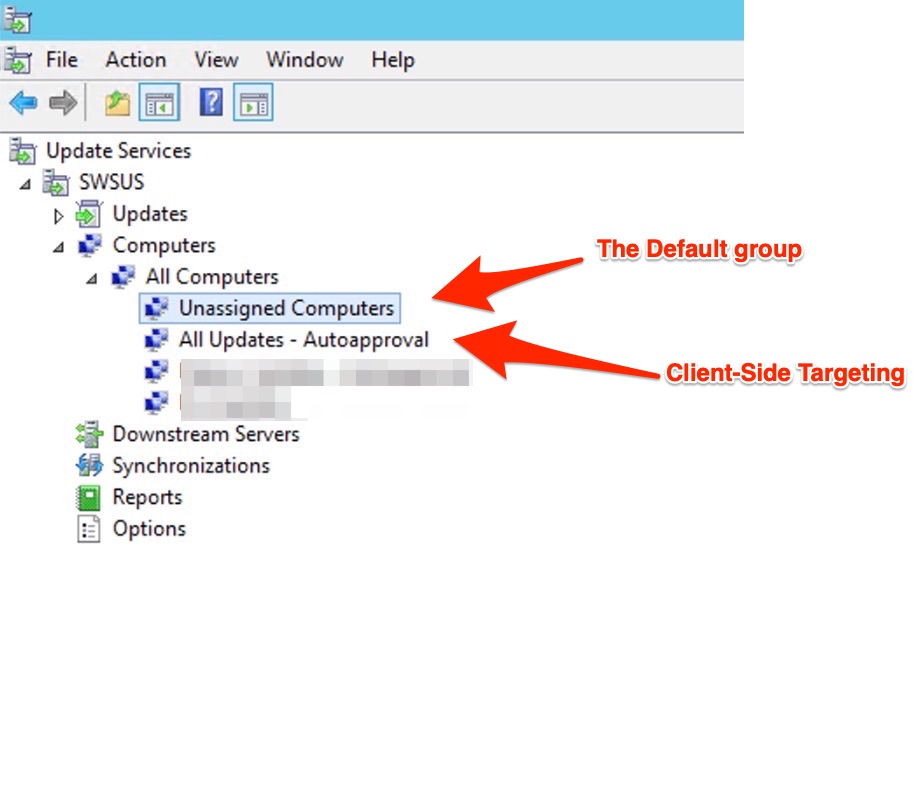
The “Client-Side Targeting”….
Normally when the computer receives the GPO policy indicating the presence of a WSUS server, the client falls back on the group (WSUS group, attention is not an AD group) called “Unassigned Computers”. But if you want, you can create a group (whatever name you want) to make computers that register for WSUS fall into this. To do this, you need to create a GPO specifying the Client Side Tagergeting that matches the name you gave the group in WSUS in my example “All Updates – Autoapproval”
Under GPO:
Under WSUS console:
At the end.. some other tips in case of problems…
In case you run into problems and your Windows 10 don’t want to know about “signing up” with your WSUS server, then use this batch to “reset” and force the client to show up to your WSUS. Run it with from a CMD with administrative rights or create a GPO (computer) that runs it as a login script created by Adam (AJ Tek)
|
1 2 3 4 5 6 7 8 9 10 11 12 |
<strong>net stop bits net stop wuauserv reg delete "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v AccountDomainSid /f reg delete "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v PingID /f reg delete "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v SusClientId /f reg delete "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v SusClientIDValidation /f rd /s /q "%SystemRoot%\SoftwareDistribution" net start bits net start wuauserv wuauclt /resetauthorization /detectnow PowerShell.exe (New-Object -ComObject Microsoft.Update.AutoUpdate).DetectNow()</strong> |
And if you have some problem upgrading from a Windows 10 build to another do some clean action with this batch:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
<strong># stopping services.... net stop wuauserv net stop cryptSvc net stop bits net stop msiserver #clean the temporary files... del "%tmp%" /s /q del "%temp%" /s /q del C:\*.tmp /s /q del C:\users\*\AppData\Local\Temp\* /s /q del C:\Windows\Temp\* /s /q # check the OS with DISM.exe # /Restorehealth to repair the corrupted scanned files # /Cleanup-image to cleanup and repair the system. # /Online you tell DISM to use the current OS and not an image. # /ResetBase to removes all superseded component in the component store Dism.exe /online /Cleanup-Image /StartComponentCleanup /ResetBase #Rename the SoftwareDistribution and System32\catroot2 net stop cryptsvc rename %systemroot%\system32\catroot2 catroot2_old rename %systemroot%\SoftwareDistribution SoftwareDistribution_old #Remove "C:\$WINDOWS.~BT" takeown /F "C:\$WINDOWS.~BT" /R /A icacls "C:\$WINDOWS.~BT\*.*" /T /grant administrators:F rmdir /S /Q "C:\$WINDOWS.~BT\" #Remove "C:\$Windows.~WS" takeown /F "C:\$Windows.~WS" /R /A icacls "C:\$WINDOWS.~BT\*.*" /T /grant administrators:F rmdir /S /Q "C:\$WINDOWS.~BT\" net start wuauserv net start cryptSvc net start bits net start msiserver exit</strong> |