This guide describe the process to join linux to an AD domain .
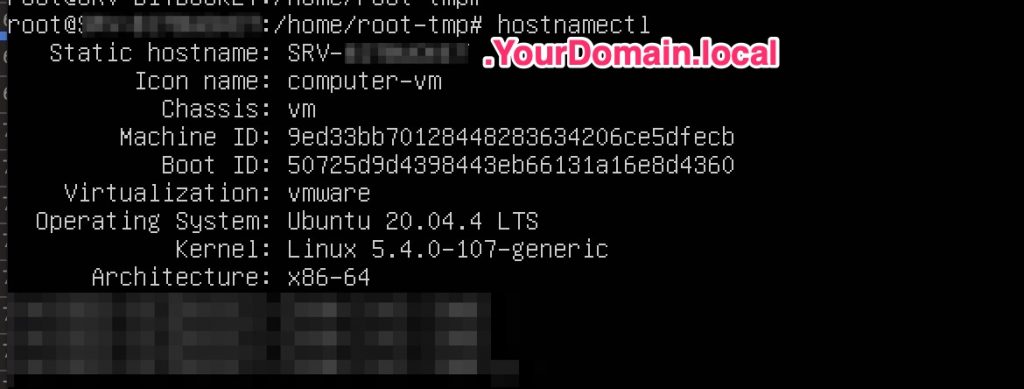
First, adapt your DNS configuration and the HOSTNAME with
|
1 |
hostnamectl set-hostname yourhostname.YourDomain.local |
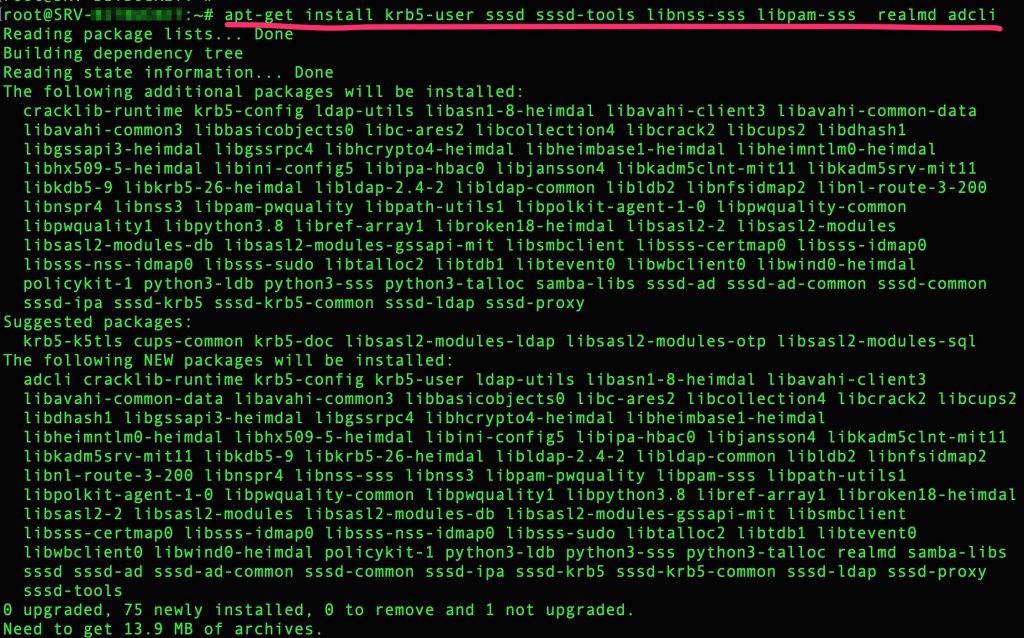
Install all the following packages :
|
1 |
apt-get install krb5-user sssd sssd-tools libnss-sss libpam-sss realmd adcli |
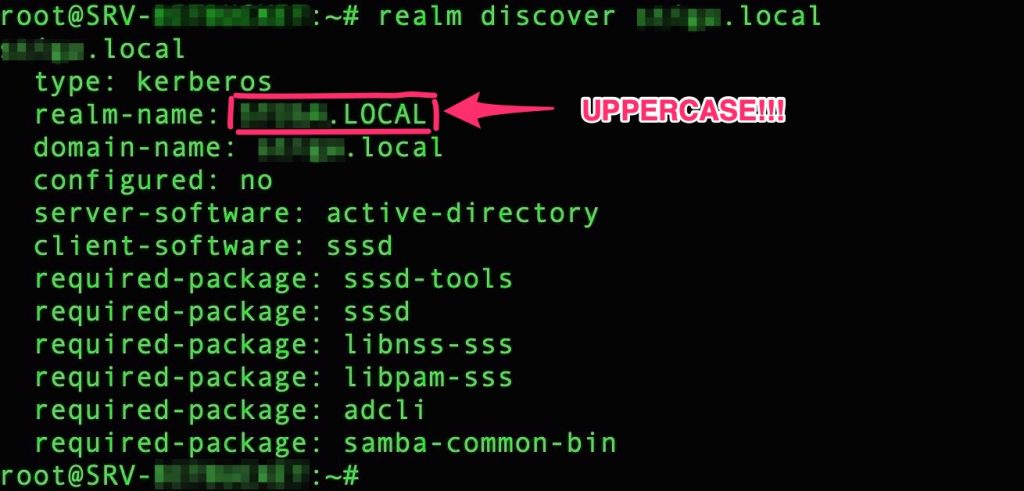
Try to contact your domain with
|
1 |
realm discover YourDoamin.local |
Now, finally, we proceed to join the domain but , first, we need to have Kerberos ticket from IT.
To do this we use “kinit” plus the realm-name that is UPPERCASE!!!
|
1 |
kinit -V DomainAdmin@YOURDOMAINALLUPPERCASE!!.LOCAL |
Now we are ready to join the domain with this command – realm reference
|
1 |
realm join --verbose YOUREALM.LOCAL -U 'DomainAdmin@YOURDOMAINALLUPPERCASE!!.LOCAL' --install=/ --computer-ou="ou=xxxx,dc=domain,dc=com" ## the OU where you want the PC object will be create |
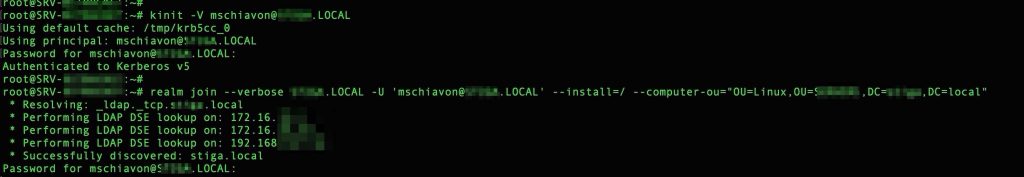
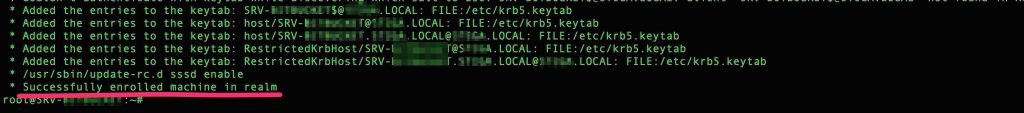
Now you are joined to the domain !!
At this point we will add
Comment /etc/sssd/sssd.conf to disable “use_fully_qualified_names” – see this reference
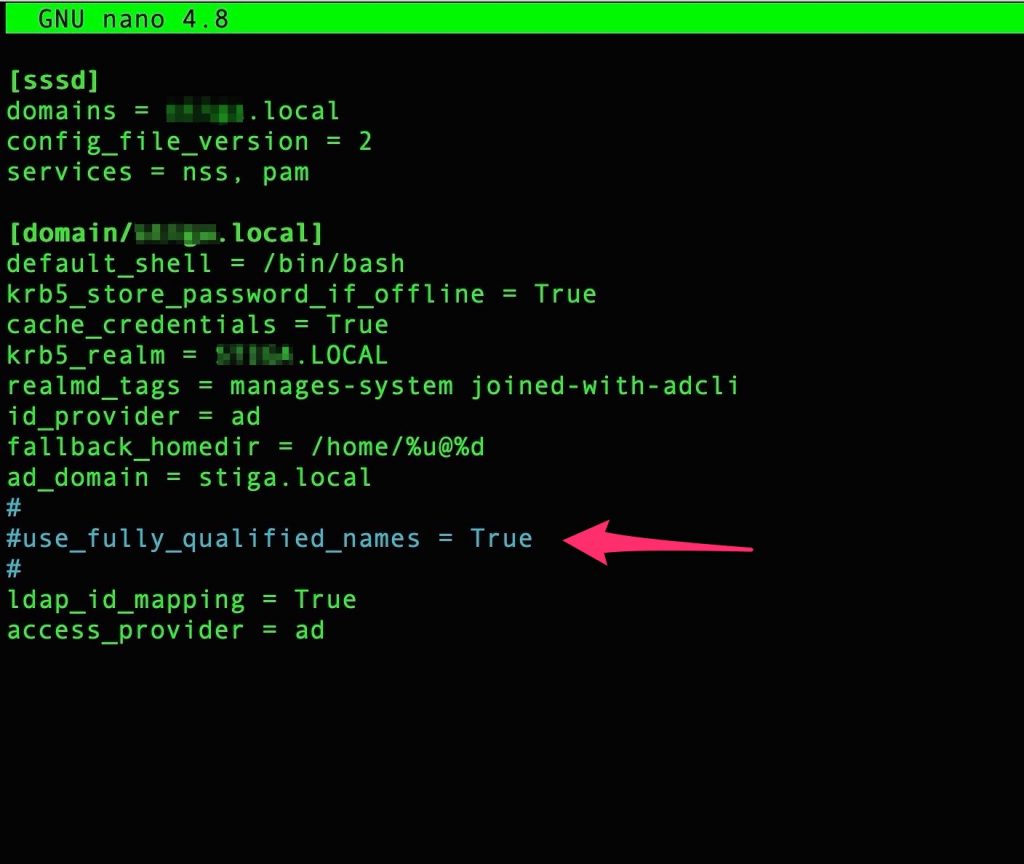
Restart “sssd”
|
1 |
systemctl restart sssd |
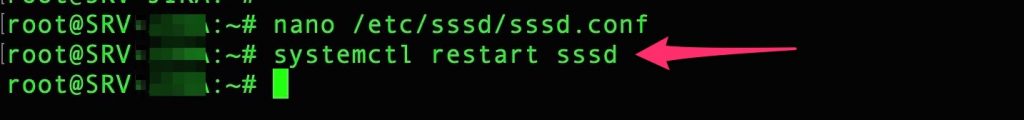
At this point modify the SSHD to permit username/password authentication
|
1 |
nano /etc/ssh/sshd_config |
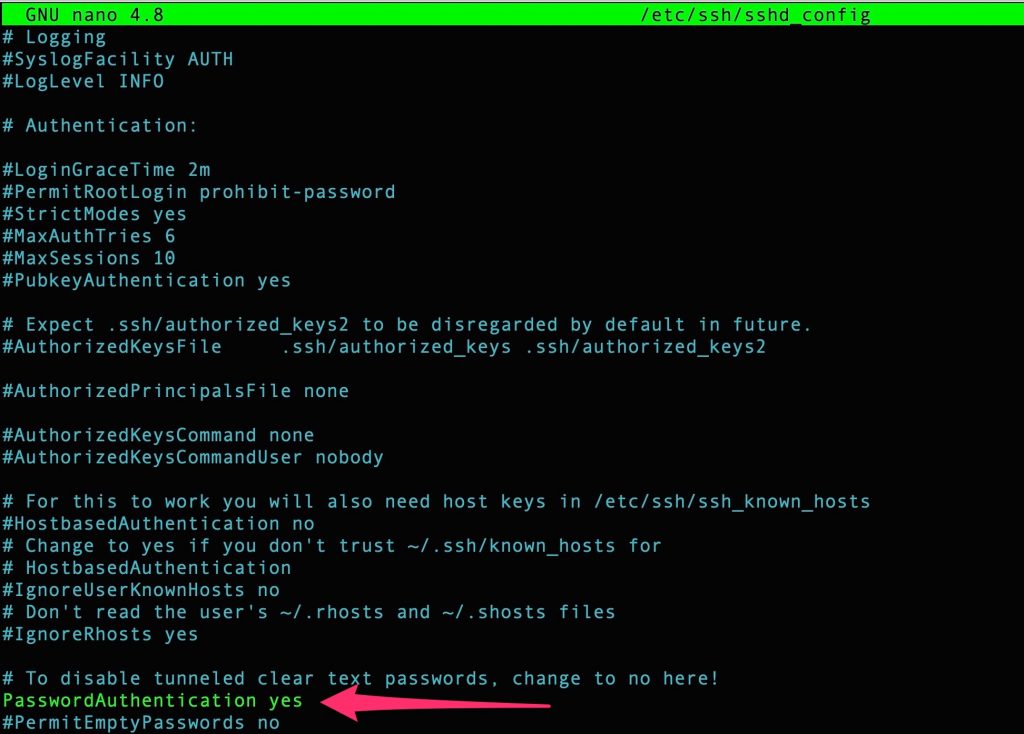
restart SSHD
|
1 |
systemctl restart sshd |
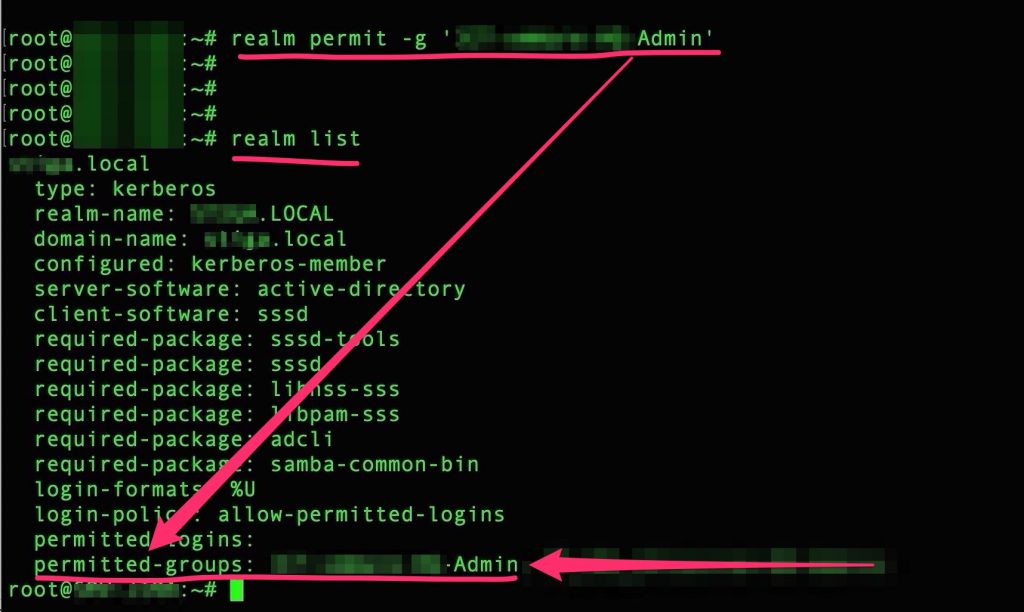
Now we need to allow SSH to specific group with this command
|
1 |
realm permit -g 'yourADGroup' |
and then, check it with this command
|
1 |
realm list |
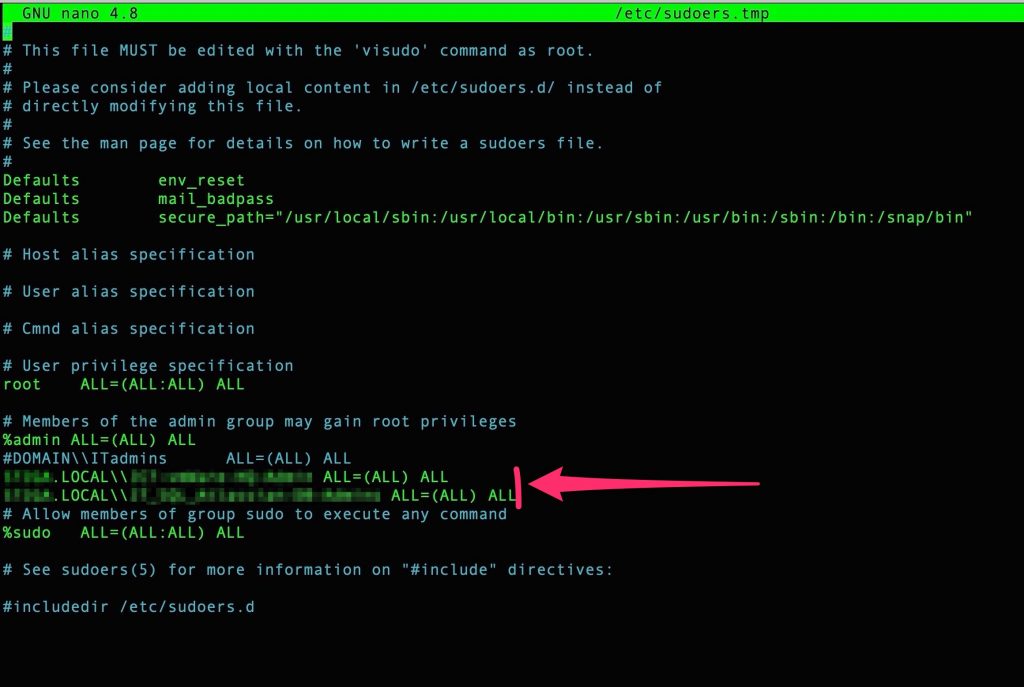
We need to grant SUDO to the user groups that we assign login permission..
edit sudoers and add group with this format => YOURDOMAIN.LOCAL\\groupname ALL=(ALL) ALL
Pay attention to spaces because you need to add escapes – see this reference
|
1 |
visudo |
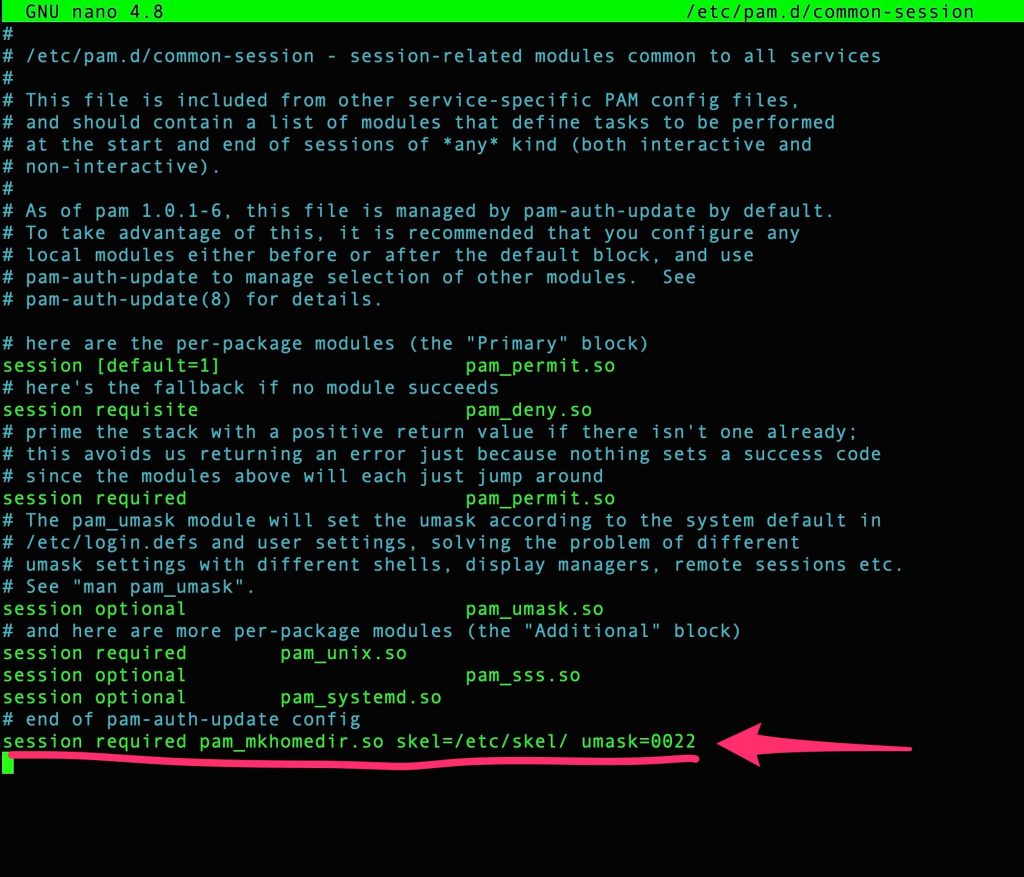
Finally, permit to Domain Users to create its home directory editing /etc/pam.d/common-session and adding :
|
1 |
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022 |
try to login trought SSH… It works!
DO YOU NEED TO DIS-JOIN ?
do this.. Some reference
|
1 |
realm leave --remove |
Now our linux is unjoined from the domain .