This lab includes the fallowing setup
| Hostname | Role |
| LAB-DC01 | Windows 2019 Standard with: AD Domain Role AD Ent Certification Authority with Enrolment Services Role |
Don’t you know if you have a Stand Alone or an Enterprise CA?
Do do this, you must have the “Enrolment Services” under Site and Services… To check this do this:
|
1 2 3 4 |
Start run =>> dssite.msc On the top "View" menu and enable "show services node" Expand the Public Key Services note and check if "Enrollment Services" exists. If so, you have an Enterprise CA otherwise no. |
First we need to create a custom model , so open Certification Authority and go to Certificate Templates, right click and open “Manage”.
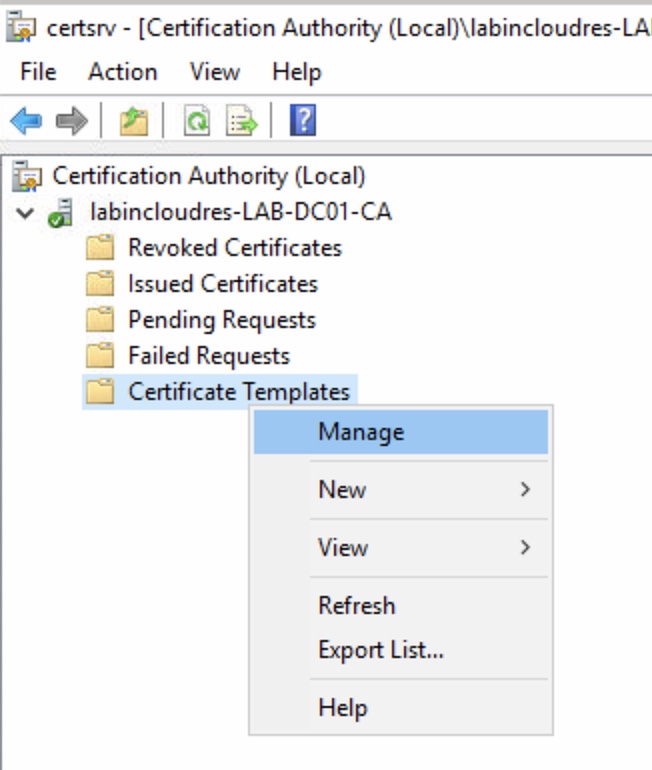
Duplicate the User template.
Change name ,and eventually the Valid and Renewal time frame.
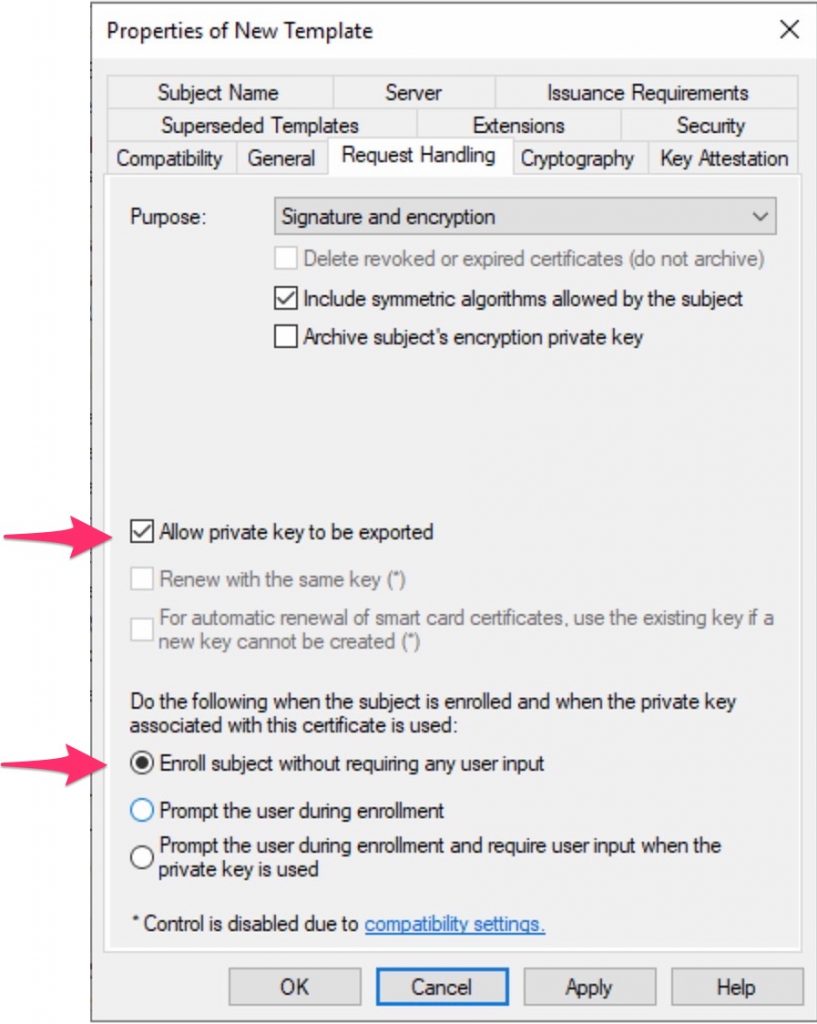
Under Request Handling, check that the key could be exported and that NO user interaction is required.
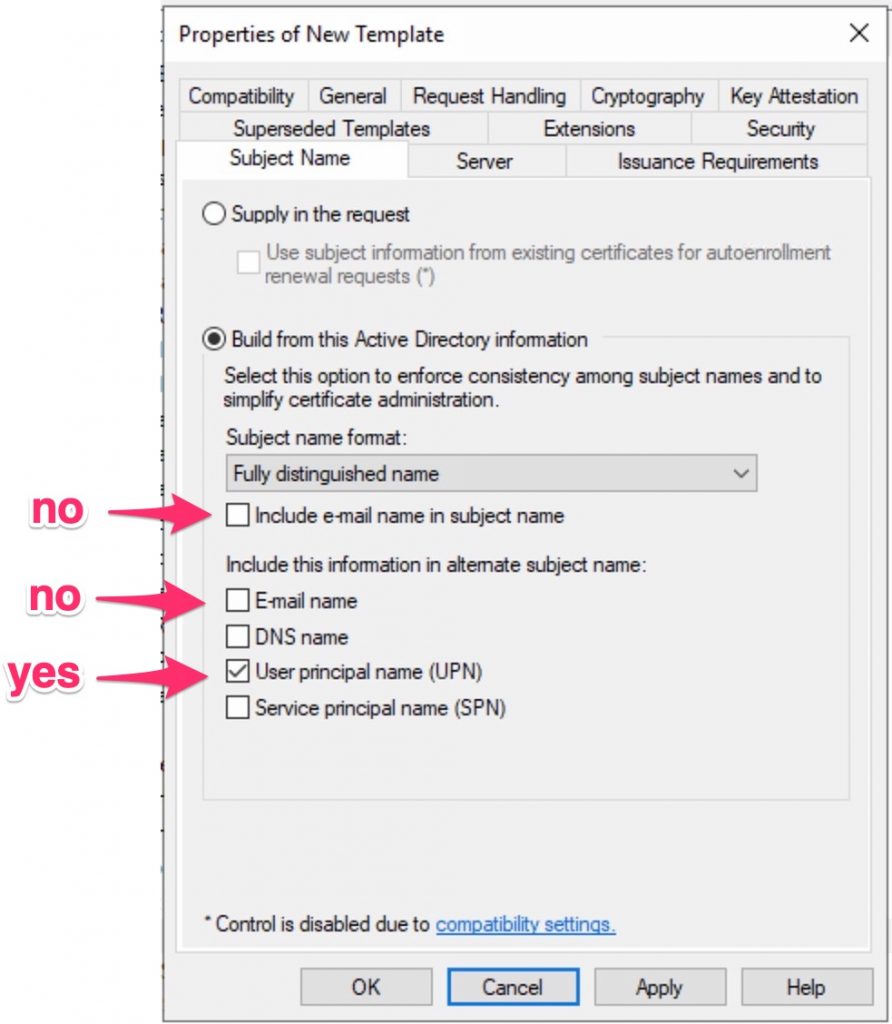
Under Subject Name, enable only this options you have .
Take in mind that if some of this settings are not populated in AD, the auto enrolment process will not work.
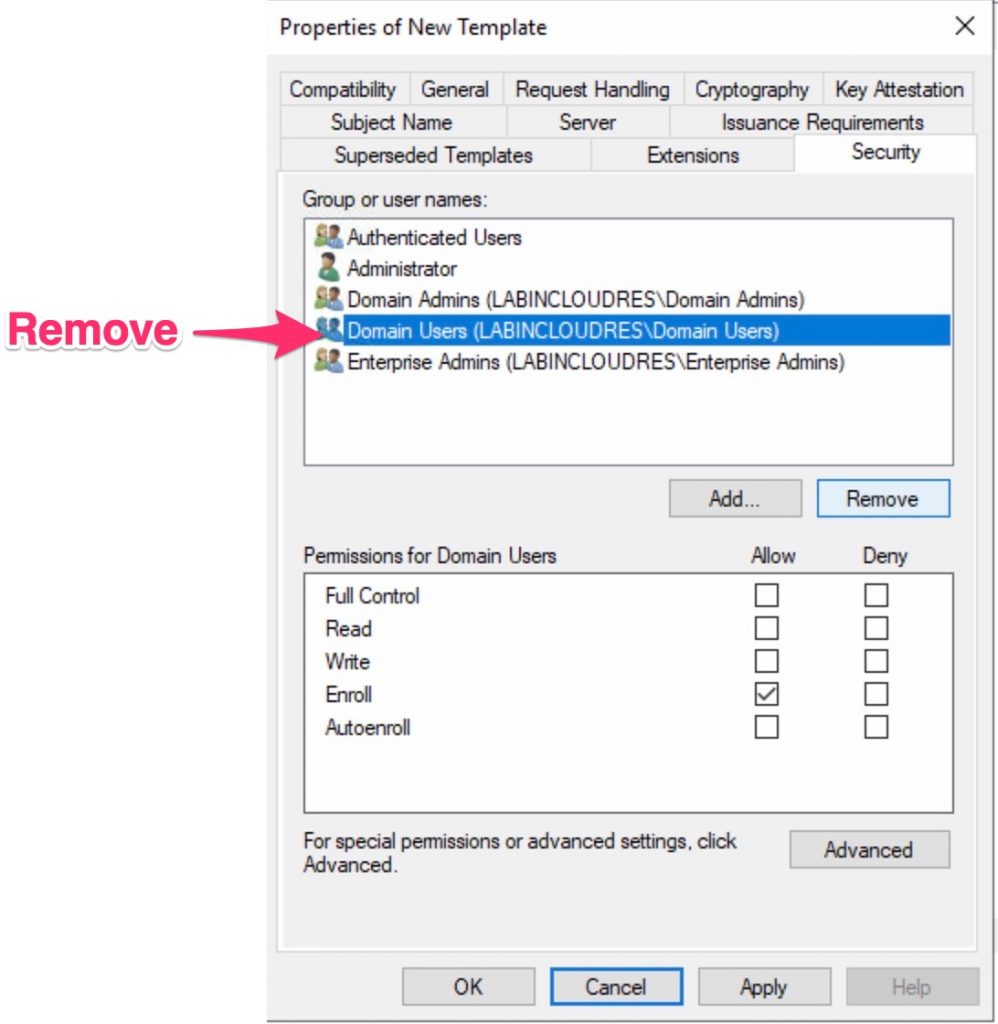
Finally, change the group assignment under Security .
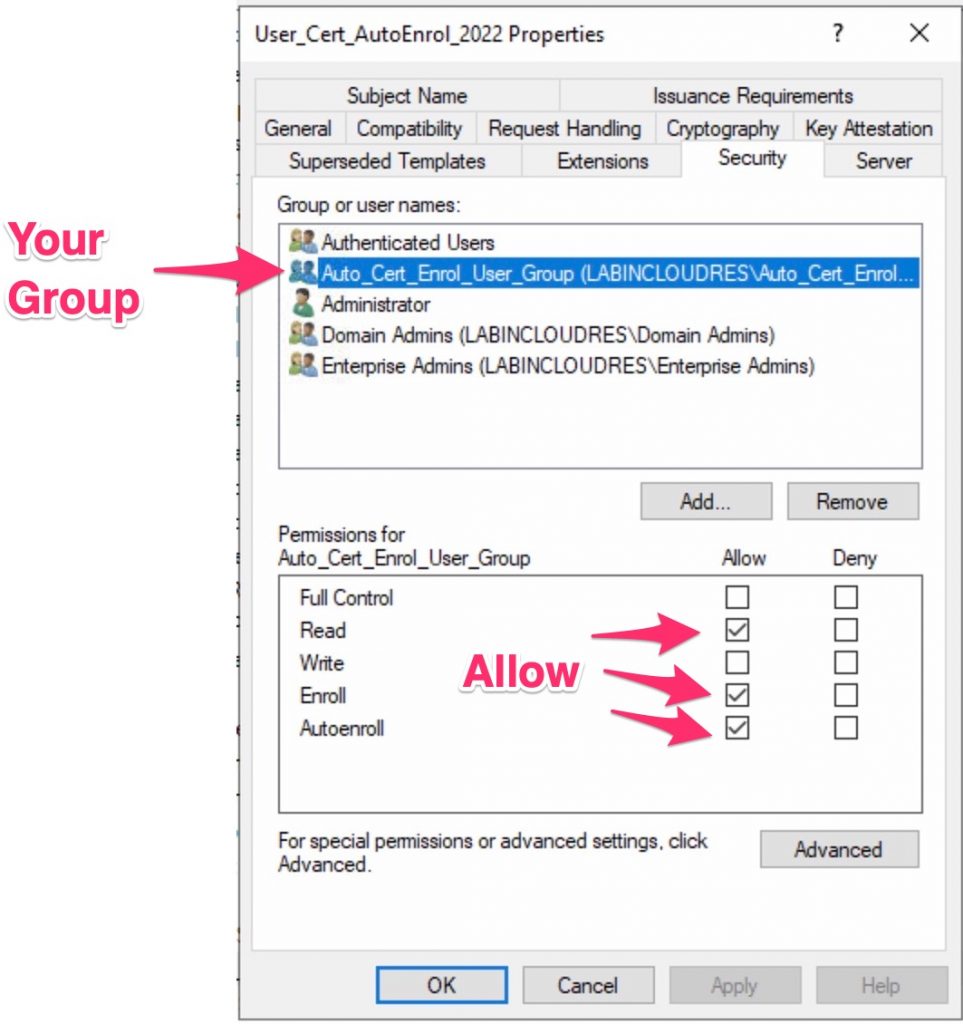
Now press OK and add this template to your CA.
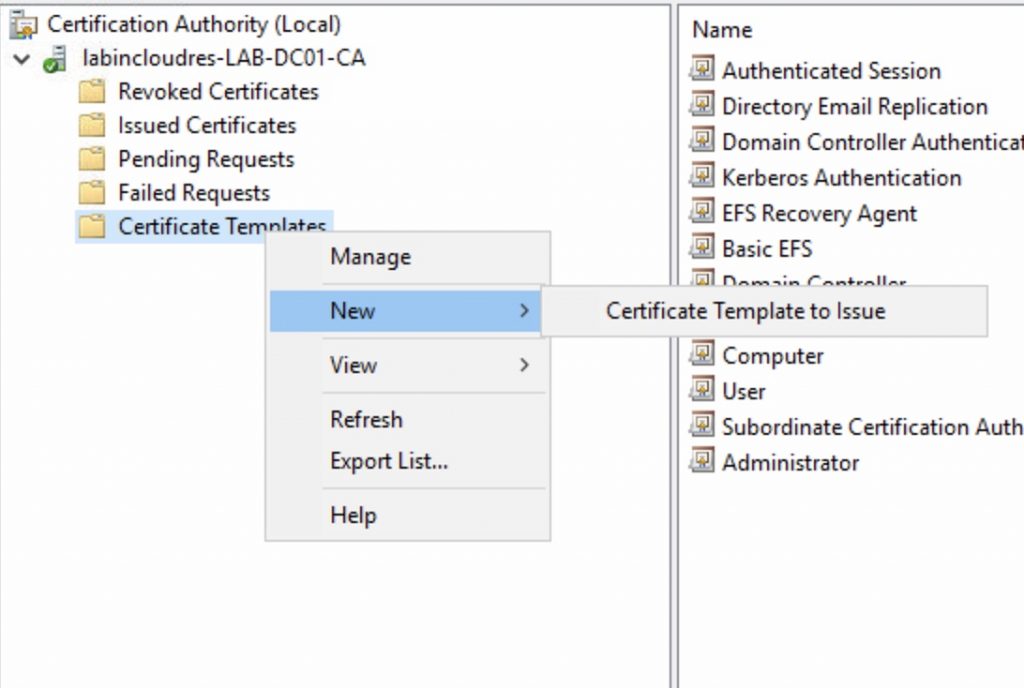
Select your template…
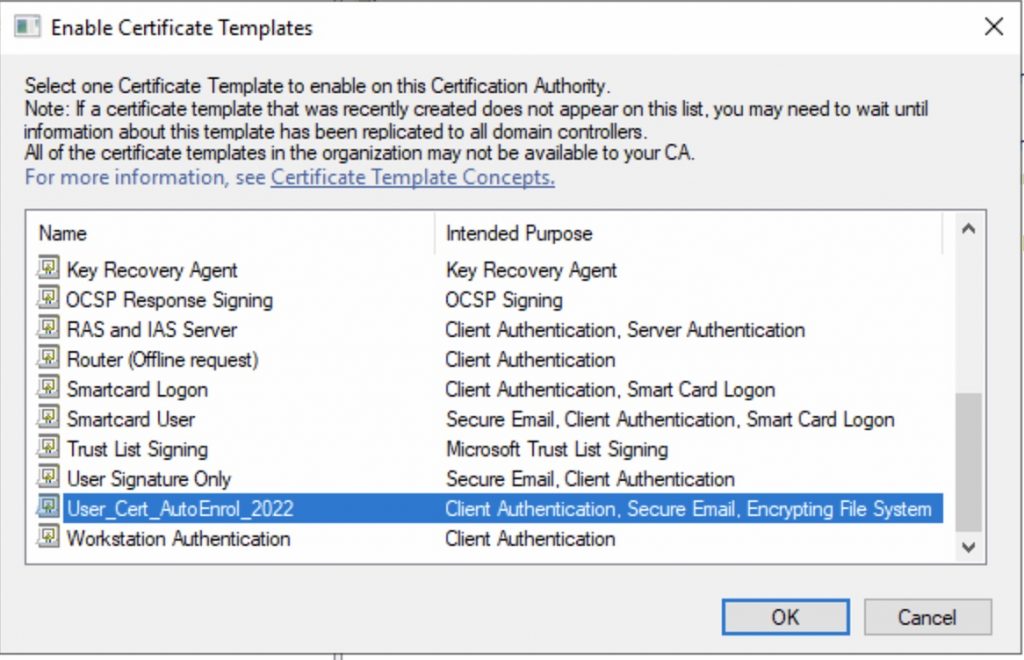
Done!
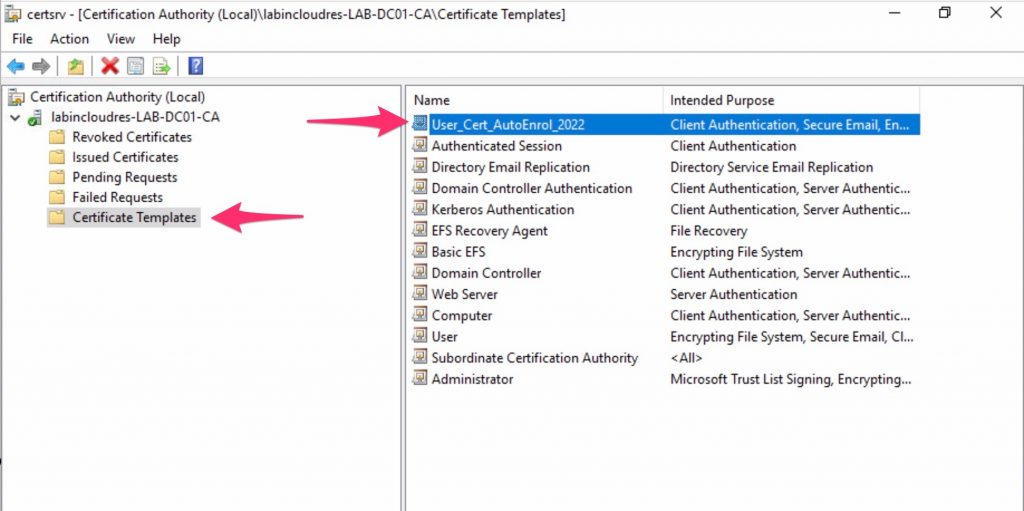
At this point we need a GPO to allow the auto-enrol of user’s cert….
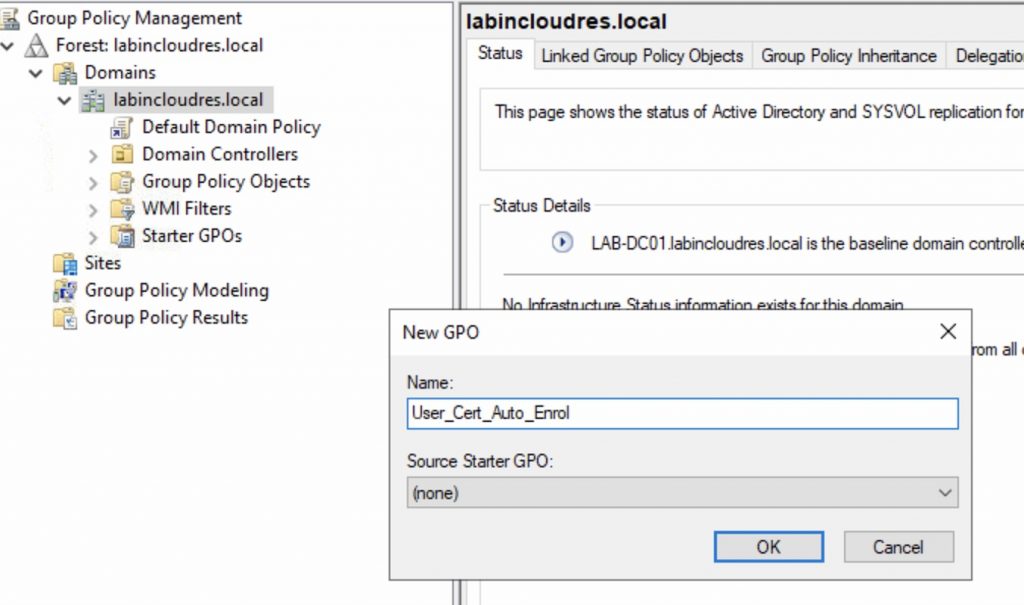
Open Group Policy Management and create a GPO linked at root level , in my case User_Cert_Auto_Enrol .
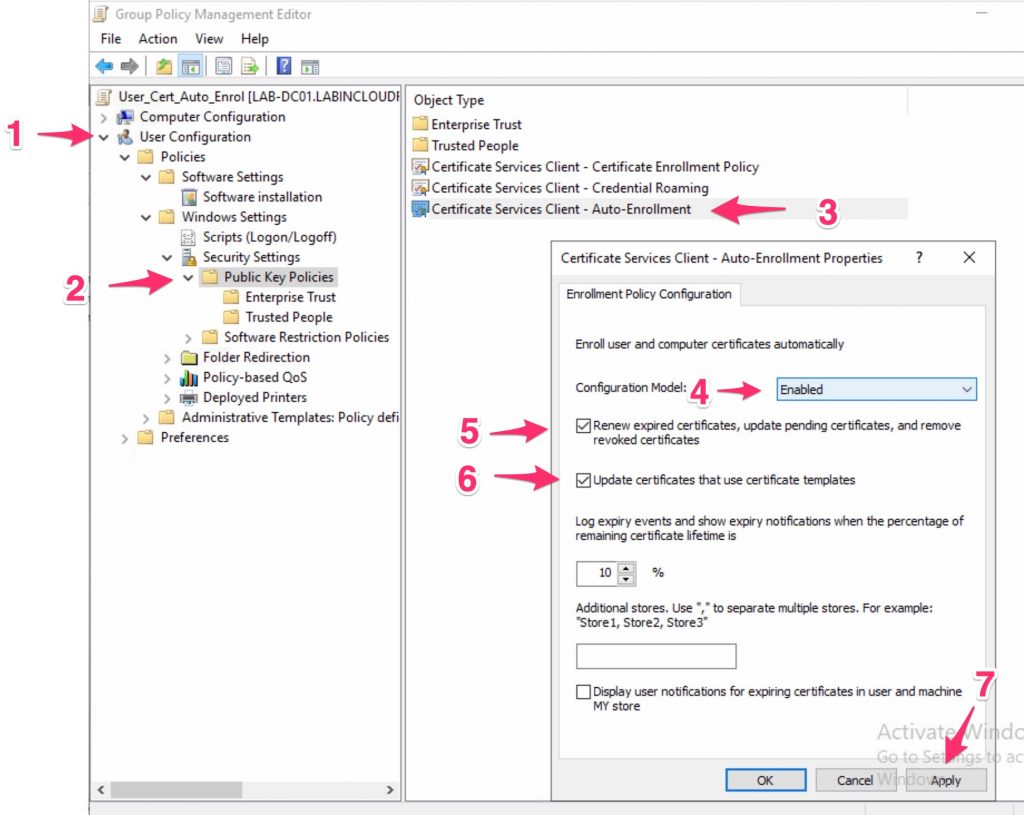
Now, edit it and enable the “user” Public Key Policies/Certificate Services Client – Auto-Enrollment Settings
At this point, add a TEST user into your security group , in my case Auto_Cert_Enrol_User_Group, login with a Windows AD joined PC and check the user personal cert….
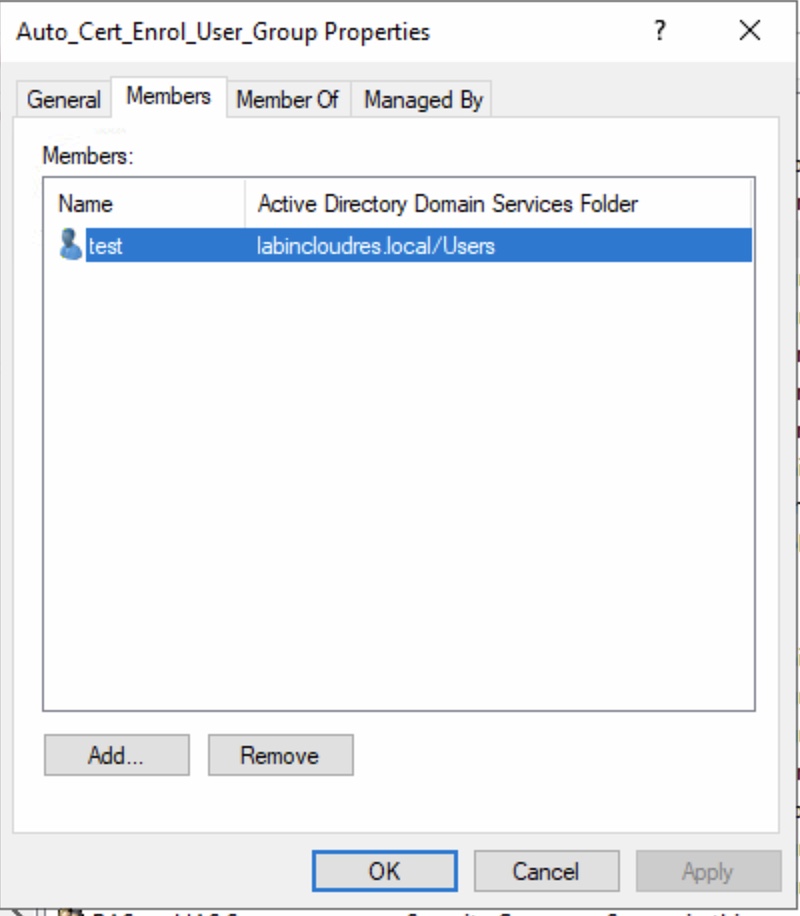
THE TEST…
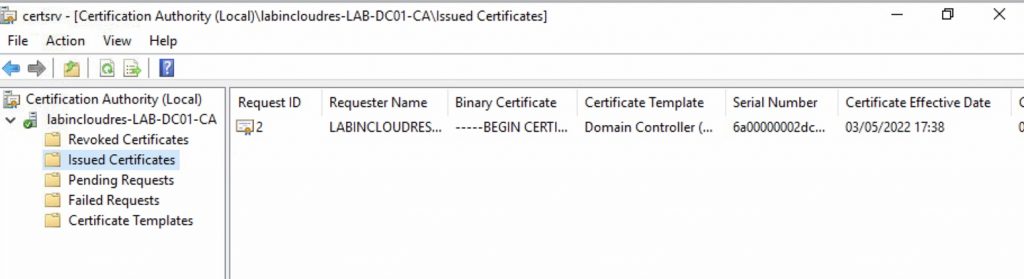
The CA before login…
Login with the user TEST…
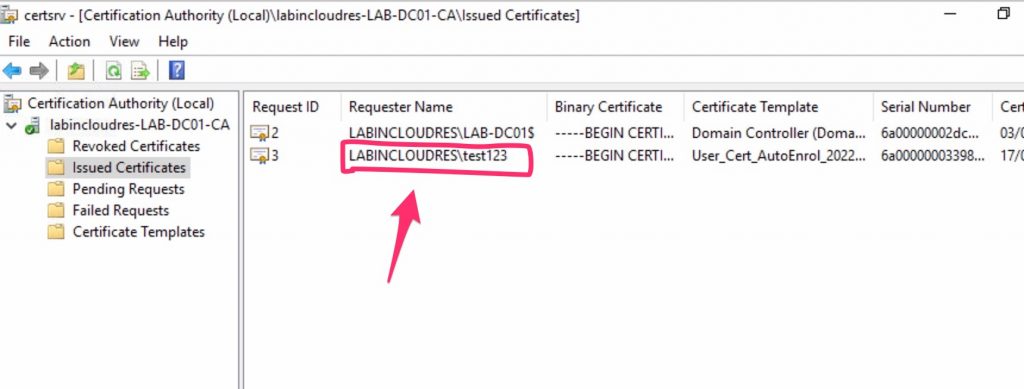
The CA after login ..
Finally, you can check it into the client with MMC => add local cert.
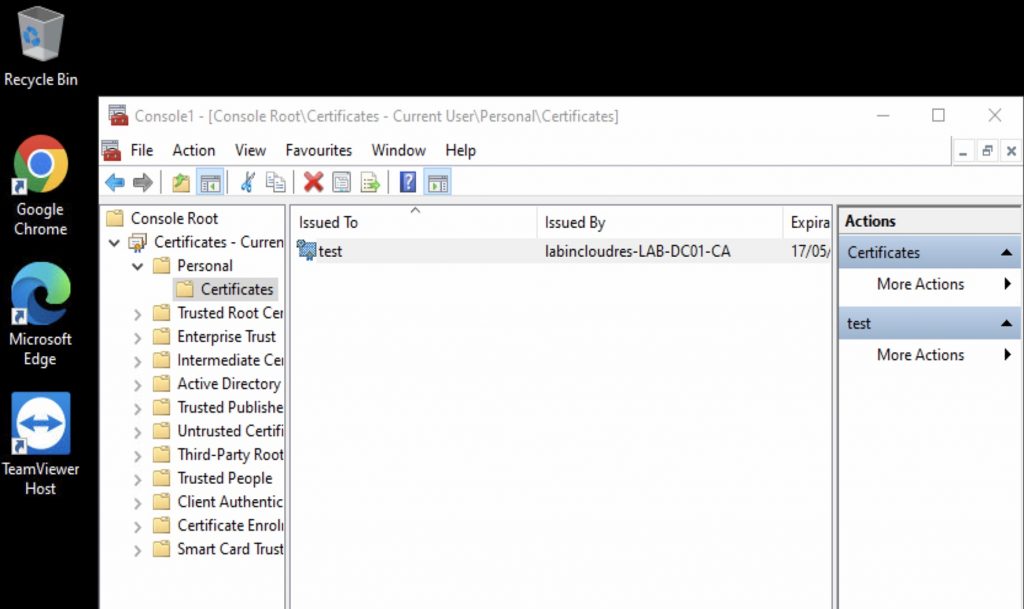
that’s it!